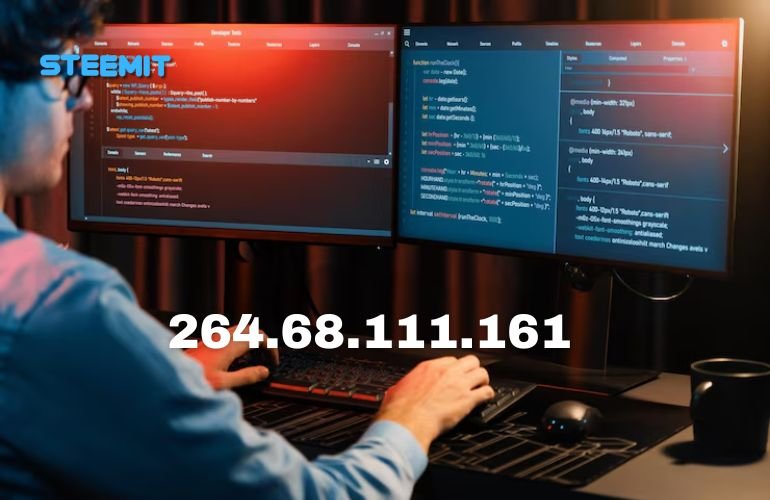
The address 264.68.111.161 might seem ordinary at first glance, but it highlights a critical lesson—not all numbers qualify as valid IPs. Understanding how these addresses work, why some fail basic checks, and their broader role in security and connectivity can clarify how the internet operates. This article explores IP fundamentals, explains common errors behind invalid examples like 264.68.111.161, and offers actionable insights for managing networks, detecting threats, and staying informed in a digitally driven world.
Breaking Down the Example: Why 264.68.111.161 Is Invalid
IPv4 Address Rules
IPv4 addresses follow a strict format: four numbers (0-255) separated by periods. Each segment, or octet, cannot exceed 255. The address 264.68.111.161 fails this rule because its first segment, 264, is outside the allowed range.
Common Causes of Invalid IPs
- Typographical Errors: Mistyping digits (e.g., entering 264 instead of 164) often creates invalid addresses.
- Misconfigured Tools: Software or scripts generating IPs automatically might produce errors if logic or bounds checks are missing.
- Copied Code or Logs: Copying IPs from code snippets or logs without verifying their validity can propagate mistakes.
Where Invalid IPs Appear
Invalid IPs like 264.68.111.161 may surface in network logs, security alerts, or debugging tools. Their presence usually signals an error in configuration, data entry, or software logic.
Risks of Ignoring Invalid IPs
Using or accepting invalid IPs can disrupt network operations. For example:
- Devices may fail to connect if configured with incorrect addresses.
- Security systems might overlook genuine threats if logs are cluttered with invalid entries.
How to Validate IP Addresses
- Manual Checks: Verify each octet falls within 0-255.
- Automated Tools: Use commands like
pingor online validators to test connectivity. - Code Sanitization: Implement input validation in software to block invalid IPs during data entry.
Fixing the Example Address
To correct 264.68.111.161, adjust the first octet to a valid value (e.g., 164.68.111.161). Always cross-reference IPs with documentation or trusted sources to avoid errors.
This section clarifies how simple oversights can create invalid IPs, why they matter, and how to resolve them effectively.
Security Implications of IP Addresses
Threats Linked to Suspicious IP Activity
Malicious actors often use IP addresses to launch attacks, spread spam, or steal data. Common threats include:
- Phishing or Fraud: Fake websites or emails originating from untrusted IPs.
- DDoS Attacks: Overloading networks by flooding target IPs with traffic.
- Unauthorized Access: Brute-force login attempts from unknown IPs.
Identifying Risky IP Behavior
Watch for patterns in logs or security tools:
- Repeated connection attempts from the same IP.
- Traffic spikes from IPs linked to known blocklists.
- Geographic mismatches (e.g., logins from distant locations).
Responding to Suspicious IPs
- Block Immediate Threats: Use firewalls or security software to restrict access from flagged IPs.
- Analyze Logs: Trace the origin and scope of suspicious activity.
- Update Defenses: Patch vulnerabilities exploited by attackers.
Tools for Monitoring IP Risks
- Firewalls: Filter traffic based on IP reputation.
- Intrusion Detection Systems (IDS): Alert on unusual IP interactions.
- Threat Intelligence Platforms: Cross-reference IPs with global threat databases.
Preventing Future Issues
- Regularly update blocklists and whitelists.
- Educate users to report unexpected network behavior.
- Conduct periodic security audits to identify exposed IPs.
Addressing IP-related risks requires proactive monitoring and swift action to minimize harm to networks and data.
Technical and Educational Uses of IP Addresses
Real-World Applications in Network Administration
IP addresses enable administrators to assign identities to devices, monitor traffic, and resolve connectivity issues. Static IPs are often reserved for critical infrastructure like servers, ensuring consistent access. Dynamic IPs, assigned via DHCP, accommodate temporary connections for devices like laptops. Tools like ping test device reachability, while traceroute maps data pathways, helping isolate bottlenecks or misconfigurations.
Learning Through Invalid IP Examples
Addresses like 264.68.111.161 are practical teaching tools. Instructors demonstrate common errors in coding or network setups, such as typos or boundary violations. Students debug scripts that generate invalid IPs, learning validation techniques like boundary checks. Research projects study patterns of invalid IPs in logs to enhance error detection algorithms.
Tools for Validating and Testing IPs
- Command-Line Utilities:
pingtests connectivity;ipconfigdisplays device IP settings. - Online Validators: Websites check if an IP follows format rules (e.g., 0-255 per octet).
- Code Sanitization: Scripts using regular expressions enforce correct IP structures, filtering invalid entries.
Case Study: Simulating Network Scenarios
Lab environments use invalid IPs to mimic real-world errors. Trainees troubleshoot simulated issues like misconfigured routers or firewall rules blocking valid traffic. These exercises build skills in diagnosing and resolving network faults efficiently.
IP addresses, even invalid ones, play distinct roles in maintaining functional networks and educating future technologists.
The Role of IP Addresses in Modern Connectivity
Geolocation and Privacy Challenges
IP addresses help approximate a device’s physical location, enabling services like local weather updates or regional content access. However, this capability raises privacy questions, as third parties can track user activity or infer habits based on location data. Advertisers, governments, or malicious actors might exploit IP geolocation for targeted campaigns, surveillance, or unauthorized profiling.
Practical Impact on Daily Internet Use
IP addresses direct data between devices, ensuring emails, websites, and streaming content reach their destinations. Unique identifiers simplify troubleshooting—for example, isolating a malfunctioning device on a network. Dynamic IPs, common in home networks, rotate to manage limited IPv4 availability, while static IPs maintain consistent access for servers or security systems.
Scalability and Protocol Evolution
The move to IPv6 addresses IPv4 shortages, supporting billions of new devices in smart homes, IoT ecosystems, and global networks. IPv6 simplifies routing, enhances security against spoofing, and eliminates workarounds like NAT (Network Address Translation). Adoption remains gradual, requiring compatibility between older and newer systems.
Balancing Innovation and Security
As connectivity expands, IP addresses remain central to emerging technologies like 5G and decentralized networks. However, their visibility exposes networks to risks like DDoS attacks or unauthorized tracking. Solutions like VPNs mask IPs for privacy, while encryption protocols safeguard data integrity during transmission.
IP addresses underpin modern digital interactions, shaping how devices communicate and services evolve. Their role will grow as global connectivity demands faster, safer, and more adaptable frameworks.
Troubleshooting and Best Practices
Resolving Invalid IP Detections

- Check Logs and Alerts: Identify patterns in network logs where invalid IPs like 264.68.111.161 appear.
- Verify Configurations: Confirm DHCP settings, static IP assignments, and subnet masks for errors.
- Use Validation Tools: Run commands like
ipconfig(Windows) orifconfig(Linux) to review device IPs. Online validators can flag format violations.
Preventing Configuration Errors
- Double-Check Entries: Manually review IPs entered in scripts, routers, or databases.
- Automate Assignments: Deploy DHCP servers to reduce manual input errors.
- Document Networks: Maintain records of IP allocations to avoid overlaps or conflicts.
Maintaining Network Hygiene
- Regular Audits: Schedule checks to update IP lists and remove outdated entries.
- Monitor Traffic: Deploy firewalls or intrusion detection systems to block suspicious IPs.
- Update Firmware: Keep routers and network devices patched to fix IP-related vulnerabilities.
When to Seek Professional Support
- Persistent connectivity issues unresolved by basic troubleshooting.
- Complex networks with VLANs, multiple subnets, or hybrid cloud setups.
- Recurring security breaches tied to unblocked malicious IPs.
Proactive troubleshooting and structured practices minimize downtime and safeguard network integrity.
Final Thoughts
IP addresses serve as the foundation of digital communication, enabling seamless interactions across devices and networks. The example of 264.68.111.161 underscores how simple errors can disrupt connectivity, while broader discussions on security, troubleshooting, and evolving protocols highlight their complexity. From identifying threats to supporting global scalability, IPs shape how data flows and systems adapt. Staying informed about their structure, risks, and applications helps users and professionals build resilient networks. As technology advances, continuous learning and adherence to best practices will remain key to navigating the challenges and opportunities these identifiers bring.